Revoked certificates when viewing mydlink cameras with-in web-browsers
12 heinäkuuta, 2018
D-Link recently discovered that two of its code signing certificates were misappropriated. Upon discovery, we immediately decommissioned the certificates and investigated the issue. Like several other companies in Asia, D-Link was victimised by a highly active cyber espionage group which has been using PLEAD Malware to steal confidential information from companies and organisations based in East Asia, particularly in Taiwan, Japan, and Hong Kong. The two affected D-Link certificates were revoked, effective July 3rd, 2018. New certificates have been issued to resolve this problem.
Accreditation and Coordination
- Anton Cherepanov, Senior Malware Researcher, ESET, llc.
- Trend Micro Incorporated
The following certificates have been revoked:
- sha1RSA certificate
‧ Issued by Symantec Class 3 SHA256 Code Signing CA
‧ Serial Number: 01 a5 86 a9 5b 44 60 9e 9f ae 25 f9 27 79 62 d6
‧ sha1 Thumbprint: 28 b7 4f b9 84 ee 71 e6 e4 04 dc c8 ce 0d c9 0d 77 43 bf a9
‧ Valid from June 22, 2018 08:00 AM PST (GMT -8:00) to September 21, 2018 07:59:59 AM PST (GMT -8:00) - sha1RSA certificate
‧ Issued by Symantec Class 3 SHA256 Code Signing CA
‧ Serial Number: 13 03 03 e4 57 0c 27 29 09 e2 65 dd b8 59 de ef
‧ sha1 Thumbprint: f0 f5 58 b8 1a f3 e9 83 a4 12 a0 f7 c8 0a c7 2a 1f ce 0c 0a
‧ Valid from September 30, 2016 8:00 AM PST (GMT -8:00) to October 01, 2019 07:59:59 AM PST (GMT -8:00)
Below is a list of affected products and estimated patch release schedule. Please note that this only affects the JAVA web-browser plug-in.
|
Model |
H/w |
Curent Ver. |
Patch Ver. |
Estimated Date |
|
DNR-312L |
Ax |
V1.07.09 |
Available |
|
|
DNR-322L |
Ax |
V2.4b03 |
V2.5b01 |
TBC |
|
DNR-322L |
Bx |
V3.01.04 |
V3.01.05 |
TBC |
|
DNR-2020-04P |
Ax |
V1.02.06 |
Available |
|
|
DNR-326 |
Ax |
V2.6b01 |
V2.7b01 |
TBC |
|
DCS-935L |
A1 |
1.11 |
1.12 |
TBC |
|
DCS-960L |
A1 |
1.06 |
1.07 |
TBC |
|
DCS-6004L |
A1 |
1.03 |
1.04 |
TBC |
|
DCS-5000L |
Ax |
1.03 |
Available |
|
|
DCS-5009L |
Ax |
1.08 |
1.09 |
TBC |
|
DCS-5010L |
Ax |
1.14 |
1.15 |
TBC |
|
DCS-5020L |
Ax |
1.14 |
Available |
|
|
DCS-5030L |
Ax |
1.04 |
1.05 |
TBC |
|
DCS-6045L |
Ax |
1.02 |
1.03 |
TBC |
|
DCS-930L |
Ax |
1.16 |
1.17 |
TBC |
|
DCS-930L |
Bx |
2.15 |
Available |
|
|
DCS-932L |
Ax |
1.14 |
1.15 |
TBC |
|
DCS-932L |
Bx |
2.16 |
Available |
|
|
DCS-933L |
Ax |
1.14 |
1.15 |
TBC |
Recommendations:
- New firmware for affected models are being developed and tested. The mydlink mobile application will notify you to update for registered cameras in the event of a new firmware release.
- This issue will not affect the mydlink mobile applications. This certificate revocation affects viewing and configuring the camera from within a web-browser.
- if you require the use of the web-browser, you can reconfigure your browser temporarily to ignore the revoked cert.
Please note regarding option 3: These settings should be treated as temporary. We recommend only reconfiguring your system during the use of the camera through a web-browser, and then returned back to default for validating the certicate.
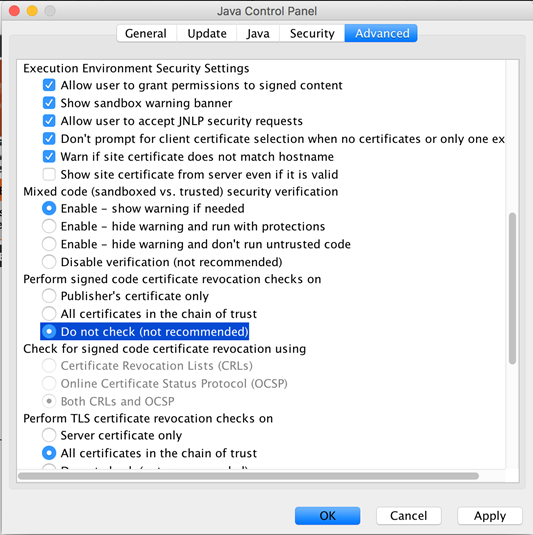
For Mac OSX:
Go System Preferences> Java> Advanced> Perform signed code certificate revocation checks on, select "Do not check (not recommended)"
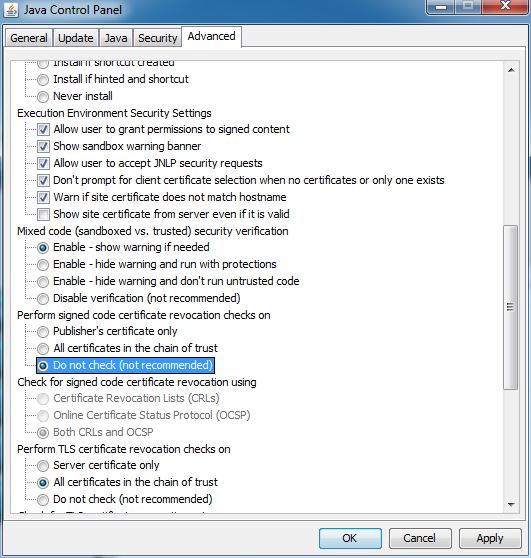
For Windows:
Go Control Panel> All Control Panel Items>Java> Advanced> Perform signed code certificate revocation checks on, select "Do not check (not recommended)"
D-Link takes the issues of network security and user privacy very seriously. We have a dedicated task force and product management team on call to address evolving security issues and implement appropriate security measures. D-Link will continuously provide updates signed using our new digital certificates.